A DNS flaw impacts a library used by millions of IoT devices
Security Affairs
MAY 3, 2022
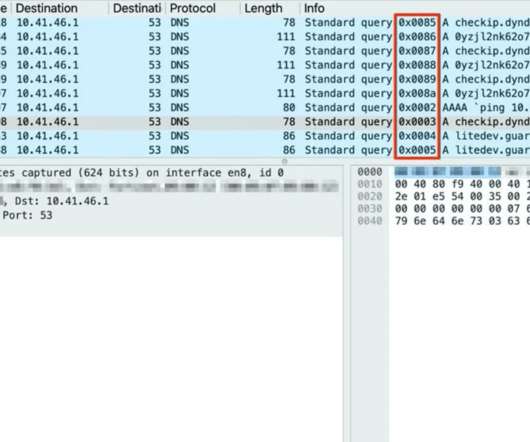
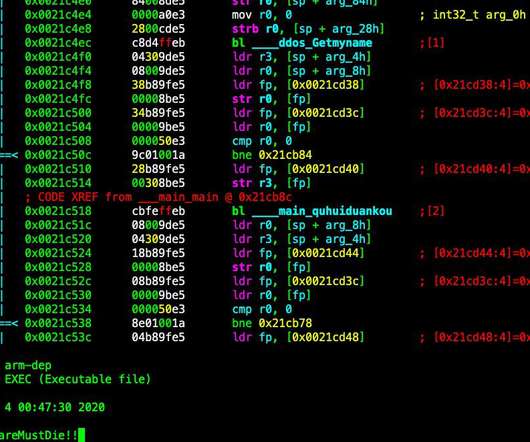
A vulnerability in the domain name system (DNS) component of the uClibc library impacts millions of IoT products. Nozomi Networks warns of a vulnerability, tracked as CVE-2022-05-02, in the domain name system (DNS) component of the uClibc library which is used by a large number of IoT products. ” concludes Nozomi.











































Let's personalize your content