Passwords Are Unfit - So Why Do We Still Have Them?
Data Breach Today
OCTOBER 4, 2022
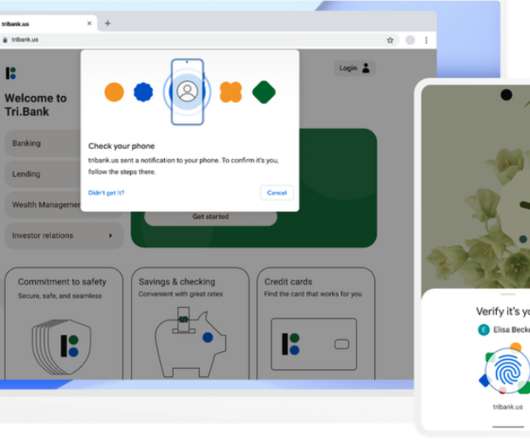
Passwords are supported everywhere. In this episode of "Cybersecurity Unplugged," Shikiar discusses how to move beyond passwords. But, says Andrew Shikiar, executive director of the FIDO Alliance, "they have been proven time and time again to simply be unfit for today's networked economy."










































Let's personalize your content