Volt Typhoon Disrupts US Organizations, CISA Issues Alerts
eSecurity Planet
FEBRUARY 16, 2024
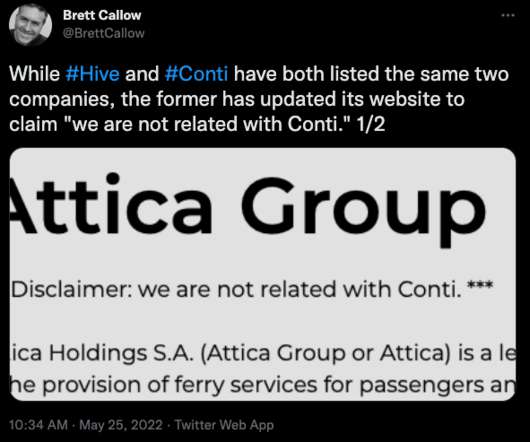
Volt Typhoon, a notorious cyber group linked to the People’s Republic of China, has expanded its operations beyond illegal access and data theft. Using web shells, they attacked weak internet servers, specifically a Houston port. critical infrastructure in the case of a major U.S.















































Let's personalize your content