FBI/AFP-Run Encrypted Phone
Schneier on Security
JUNE 11, 2021
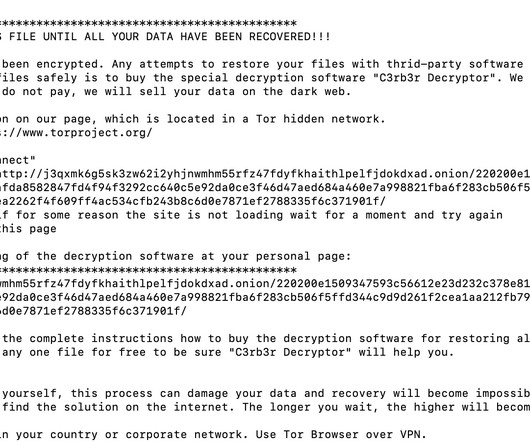
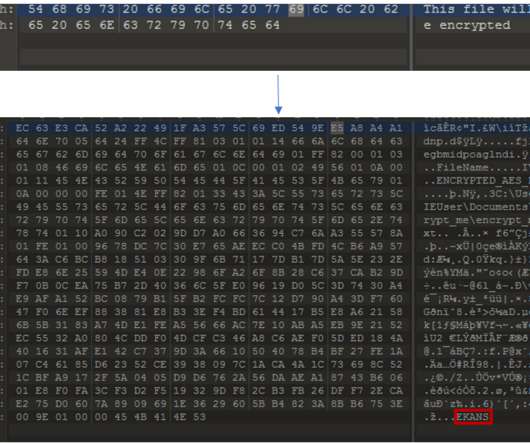
For three years, the Federal Bureau of Investigation and the Australian Federal Police owned and operated a commercial encrypted phone app, called AN0M, that was used by organized crime around the world. Of course, the police were able to read everything — I don’t even know if this qualifies as a backdoor.













































Let's personalize your content