Arrests and Indictments in LockBit Crackdown
Data Breach Today
FEBRUARY 20, 2024
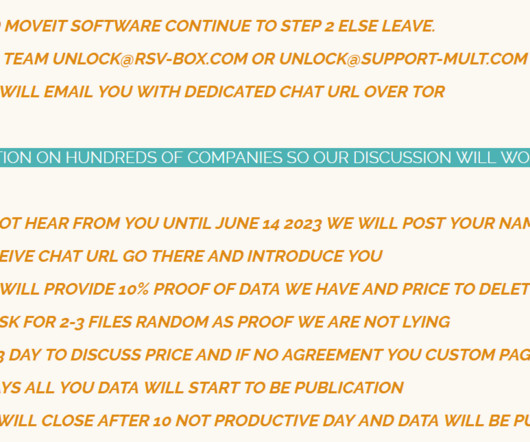
US, UK and European Authorities Seize Decryption Keys and Will Contact Victims An international law enforcement operation that infiltrated ransomware-as-a-service operation LockBit has resulted in arrests, indictments and the seizure of encryption keys that can be used to help victims recover their data.












































Let's personalize your content