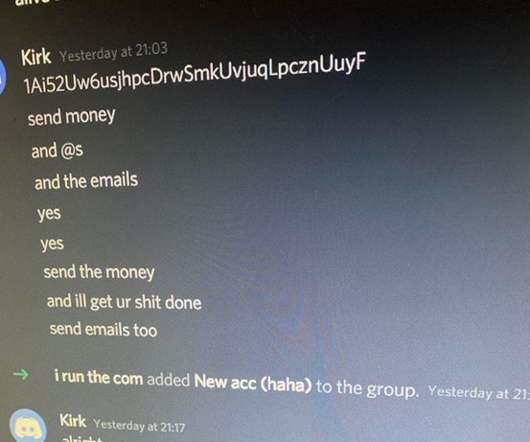
Note to Self: Create Non-Exhaustive List of Competitors
Krebs on Security
APRIL 20, 2021
Mine was learning that KrebsOnSecurity is listed as a restricted competitor by Gartner Inc. NYSE:IT ] — a $4 billion technology goliath whose analyst reports can move markets and shape the IT industry. The bulk of Gartner’s revenue comes from subscription-based IT market research.






























Let's personalize your content