ToxicEye RAT exploits Telegram communications to steal data from victims
Security Affairs
APRIL 24, 2021
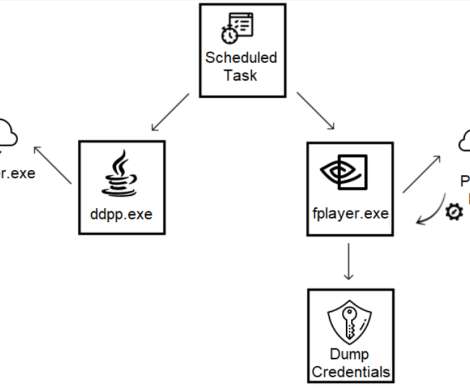
Telegram is a legitimate service and enterprise AV engines and security solutions trust its traffic. “The bot is embedded into the ToxicEye RAT configuration file and compiled into an executable file (an example of a file name we found was ‘paypal checker by saint.exe’). Pierluigi Paganini.





























Let's personalize your content