China-linked APT41 group targets Hong Kong with Spyder Loader
Security Affairs
OCTOBER 18, 2022
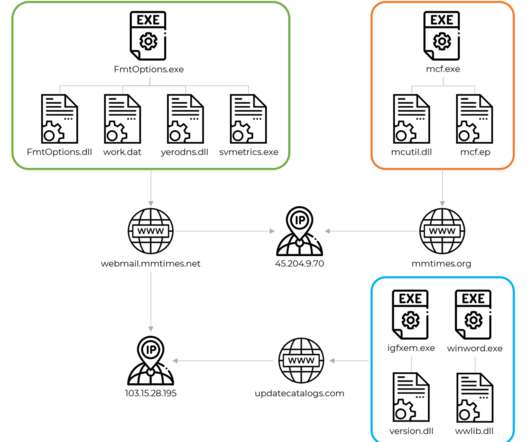
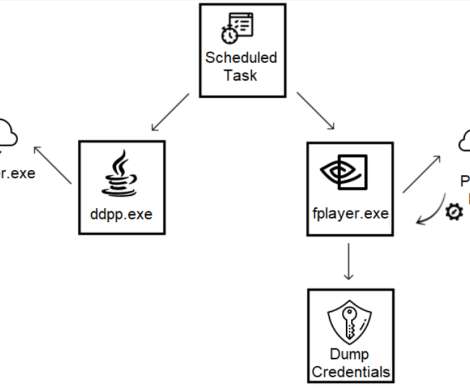
Like the sample analyzed by Cyberreason, the Spyder Loader sample analyzed by Symantec uses the CryptoPP C++ library. To prevent analysis, the malware also cleans up created artifacts, overwriting the content of the dropped wlbsctrl.dll file before deleting it. . ” continues the report. Pierluigi Paganini.



















Let's personalize your content