New RedLine malware version distributed as fake Omicron stat counter
Security Affairs
JANUARY 12, 2022
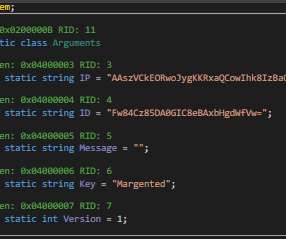
The new variant discovered by Fortinet has the file name “Omicron Stats.exe,” threat actors are attempting to exploit the enormous interest on a global scale on the COVID-19 Omicron variant. Over the course of the few weeks after this variant was released, we noticed one IP address in particular communicating with this C2 server.”













Let's personalize your content