BlackWater, a malware that uses Cloudflare Workers for C2 Communication
Security Affairs
MARCH 15, 2020
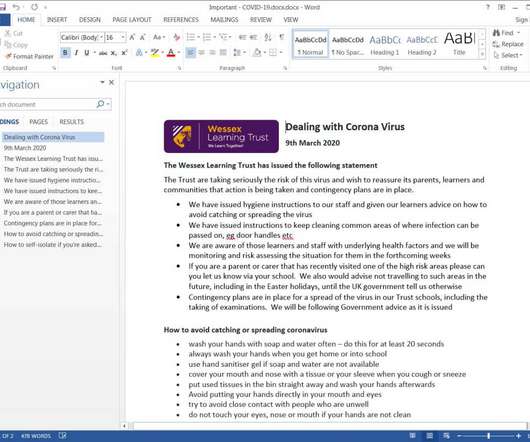
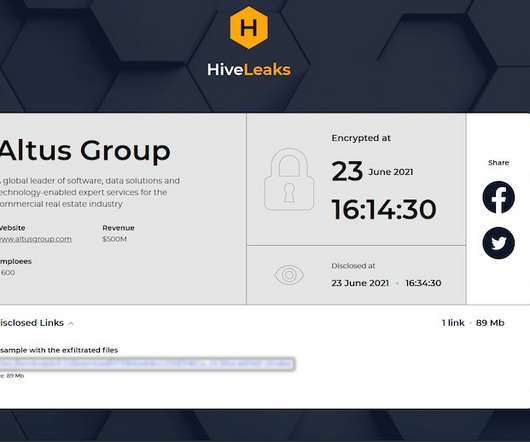
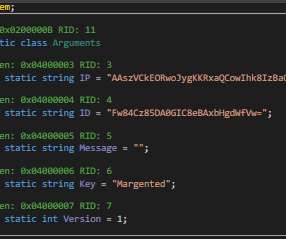
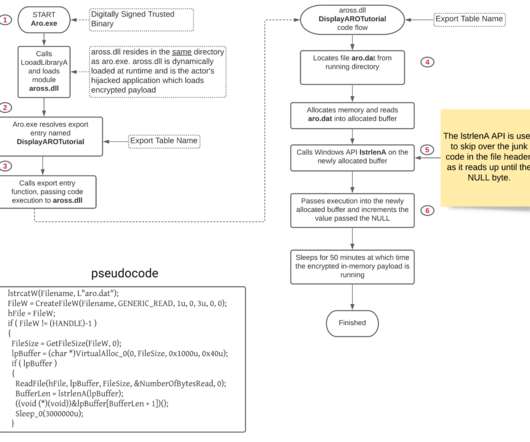
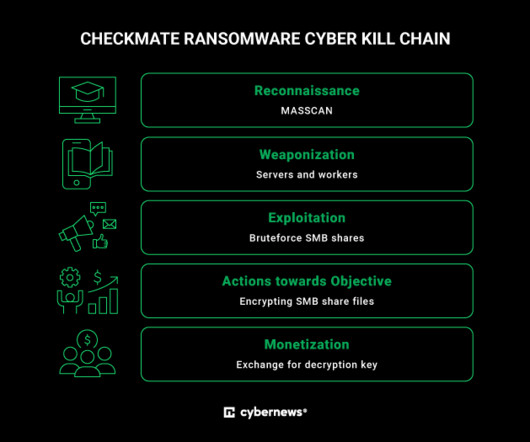
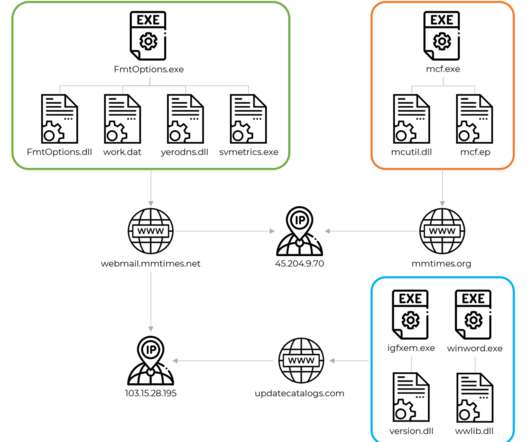
Researchers from MalwareHunterTeam discovered a suspicious RAR file named “COVID-19-” that was being distributed online, likely through phishing emails. "Important The RAR archive contains a file named “Important – COVID-19” that displays a Word icon. "Important – COVID-19.rar"






























Let's personalize your content