Will cryptocurrency mining soon saturate AWS, Microsoft Azure and Google Cloud?
The Last Watchdog
JUNE 20, 2018
Don’t look now but cryptojacking may be about to metastasize into the scourge of cloud services. You can mine them, if you have a powerful CPU. Or you can hijack other people’s computers to do the mining. However, closer inspection reveals how cryptojacking morphed out of the ransomware plague of 2015 and 2016.


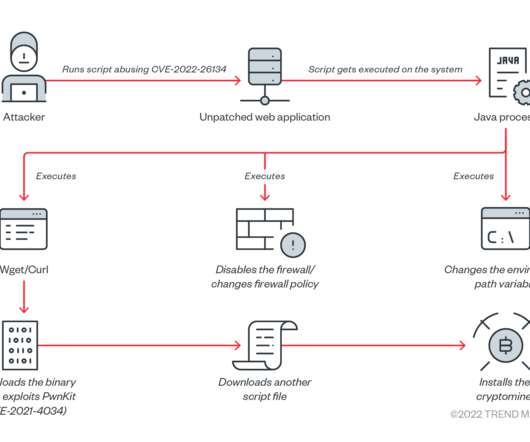

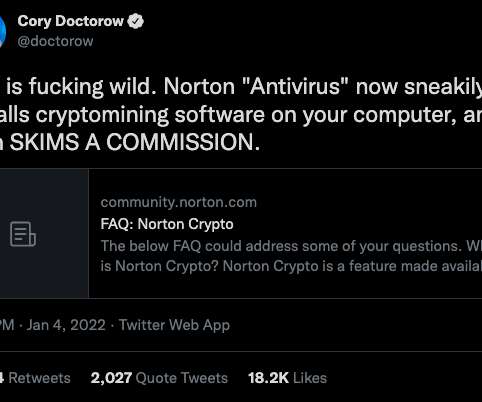




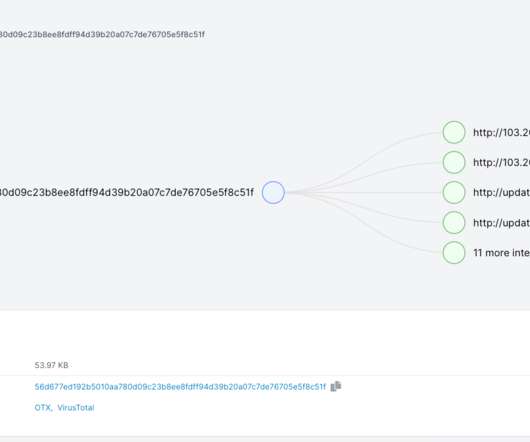

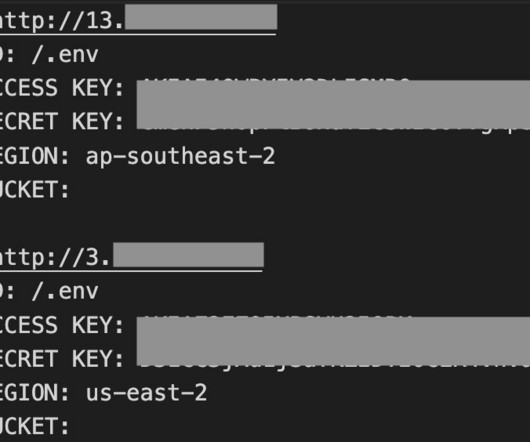


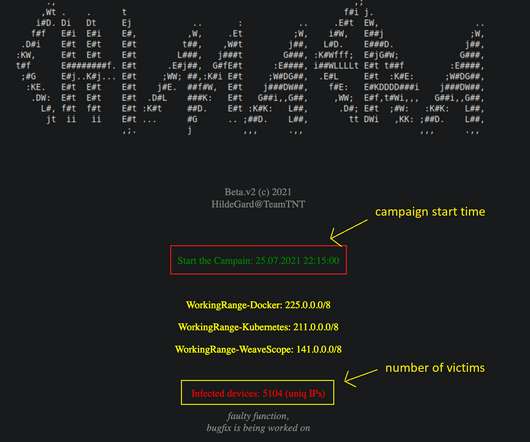


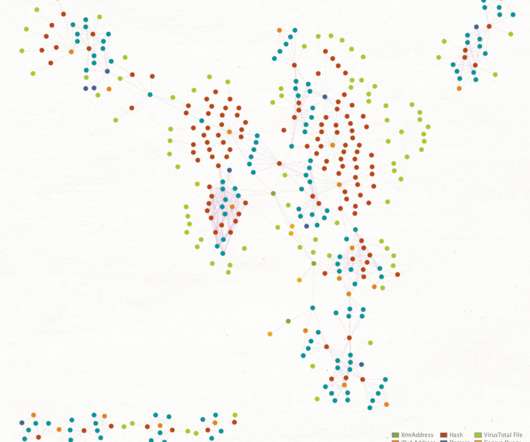



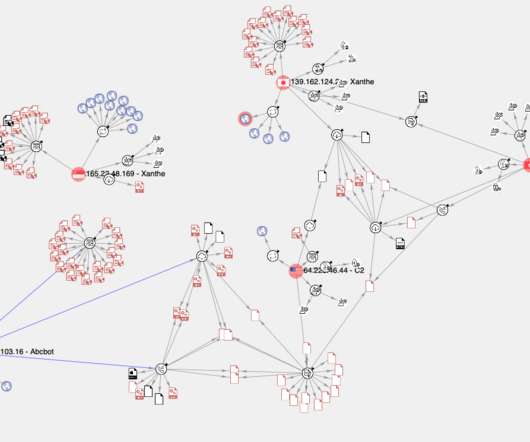






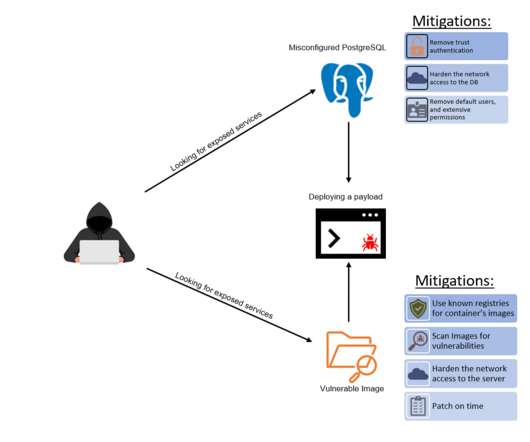



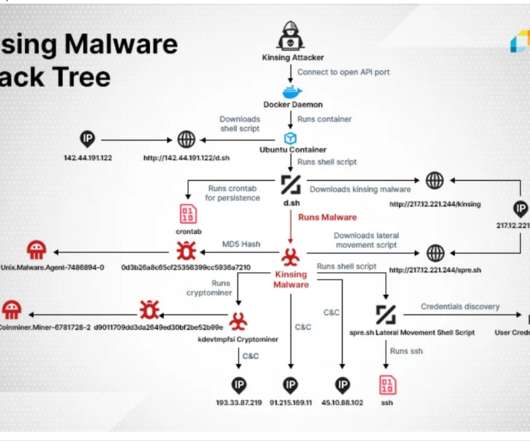

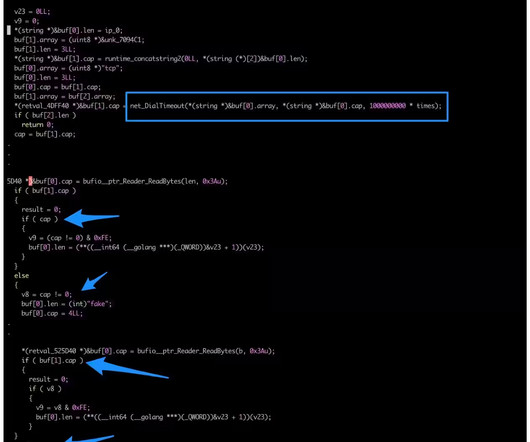

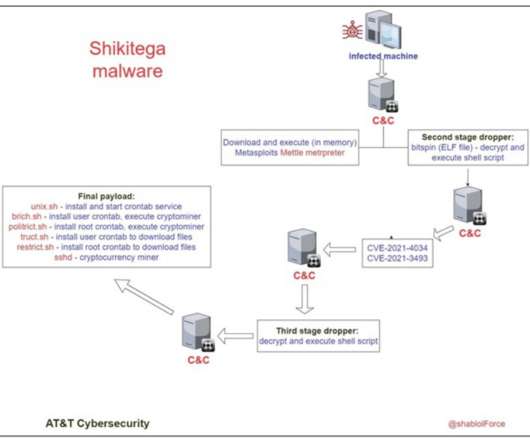








Let's personalize your content