STEPS FORWARD Q&A: Will ‘proactive security’ engender a shift to risk-based network protection?
The Last Watchdog
OCTOBER 4, 2023
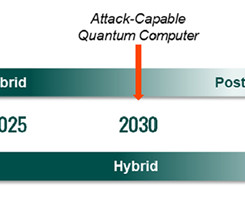
Something simply must be done to slow, and ultimately reverse, attack surface expansion. Companies are obsessed with leveraging cloud-hosted IT infrastructure and the speedy software development and deployment that goes along with that. Here’s what he had to say: LW: What is ‘proactive security’ and why is it gaining traction?

















































Let's personalize your content