Streamlining Data Collection for Investigations and eDiscovery
OpenText Information Management
SEPTEMBER 22, 2023
Additionally, the risks associated with protecting that data have never been higher, due to strengthened data privacy laws worldwide and increasing cyberattacks on businesses everywhere.





















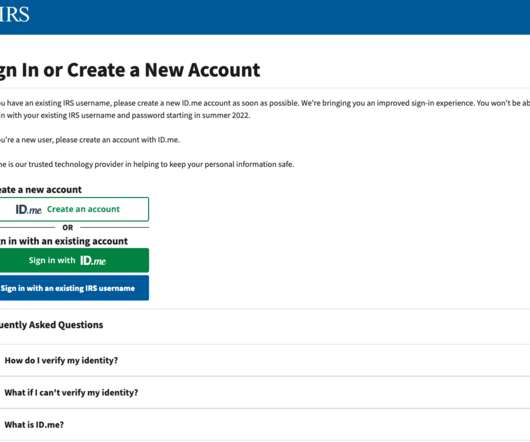







Let's personalize your content