The Rise of One-Time Password Interception Bots
Krebs on Security
SEPTEMBER 29, 2021
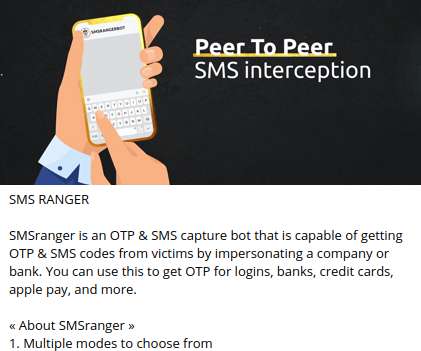
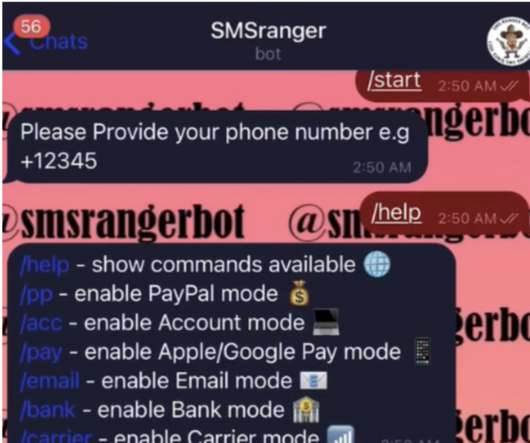
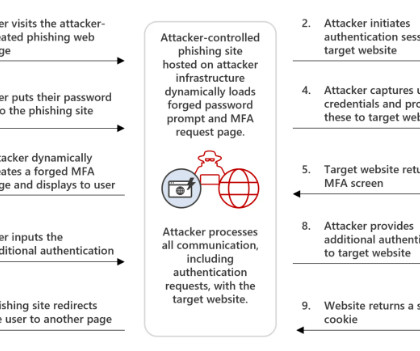
In February, KrebsOnSecurity wrote about a novel cybercrime service that helped attackers intercept the one-time passwords (OTPs) that many websites require as a second authentication factor in addition to passwords. An ad for the OTP interception service/bot “SMSRanger.”














































Let's personalize your content