Attackers Use Bots to Circumvent Some Two-Factor Authentication Systems
eSecurity Planet
SEPTEMBER 30, 2021
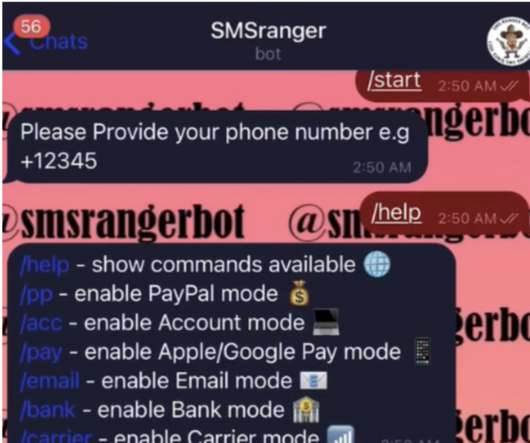
Underground services are cropping up that are designed to enable bad actors to intercept one-time passwords (OTPs), which are widely used in two-factor authentication programs whose purpose is to better protect customers’ online accounts. By using the services, cybercriminals can gain access to victims’ accounts to steal money.















































Let's personalize your content