W4SP Stealer Stings Python Developers in Supply Chain Attack
Dark Reading
NOVEMBER 4, 2022
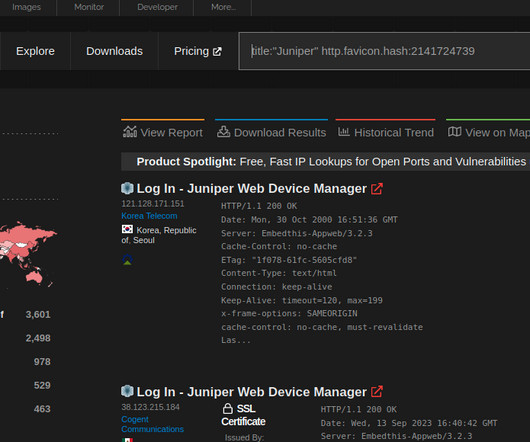
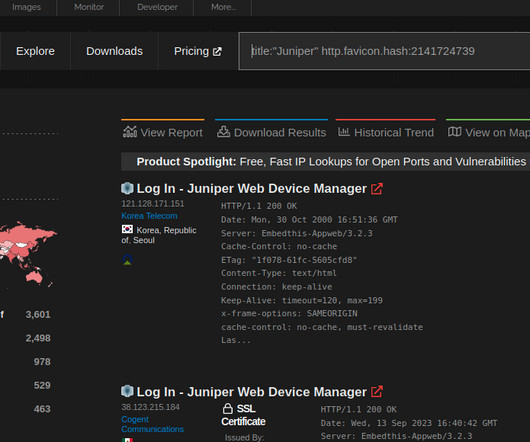
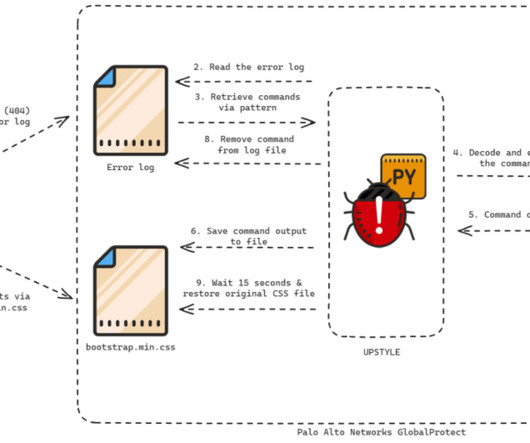
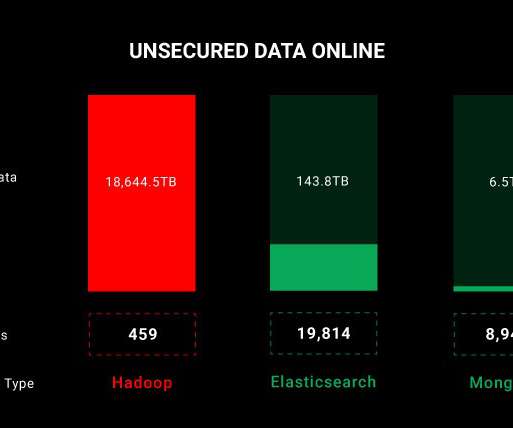
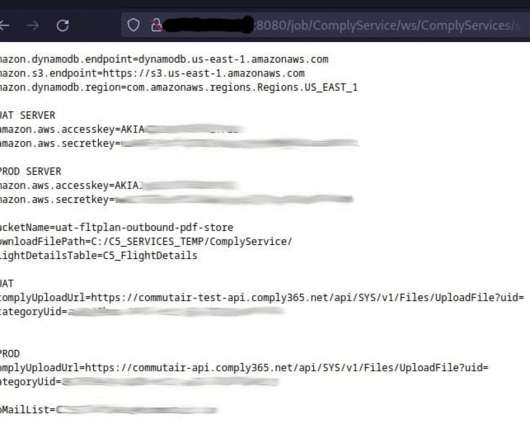
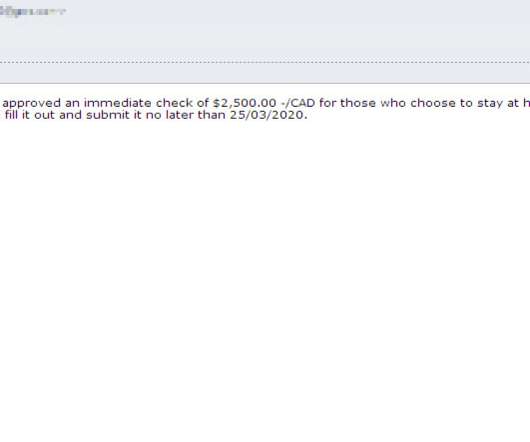
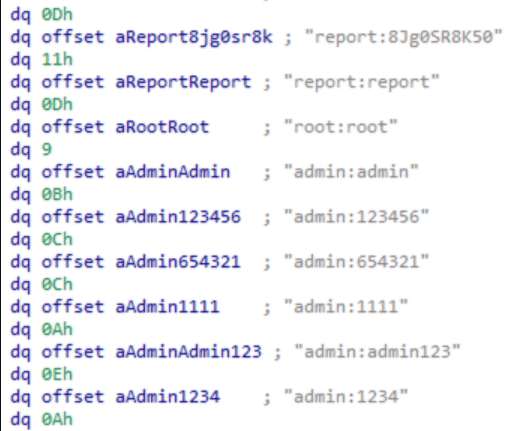
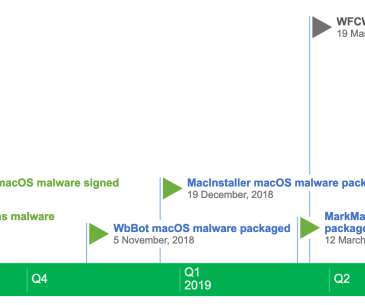
Threat actors continue to push malicious Python packages to the popular PyPI service, striking with typosquatting, authentic sounding file names, and hidden imports to fool developers and steal their information.
































Let's personalize your content