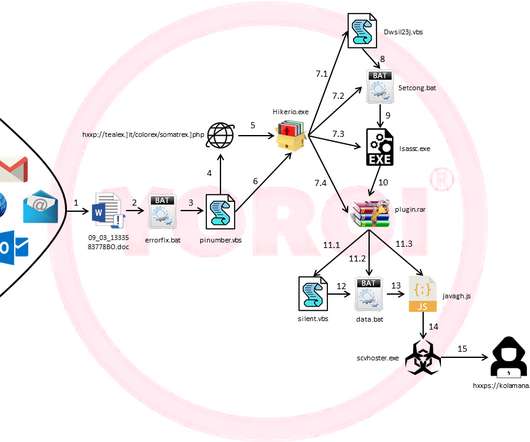
IT Army of Ukraine gained access to a 1.5GB archive from Gazprom
Security Affairs
JANUARY 31, 2023
GB archive. GB archive belonging to the Russian energy giant Gazprom. The group of hacktivists announced the hack on their Telegram channel claiming that the archive contains more than 6,000 files of the companies of the Gazprom group. “The archive with a capacity of 1.5 “The archive with a capacity of 1.5
























Let's personalize your content