Russia-linked APT28 and crooks are still using the Moobot botnet
Security Affairs
MAY 3, 2024
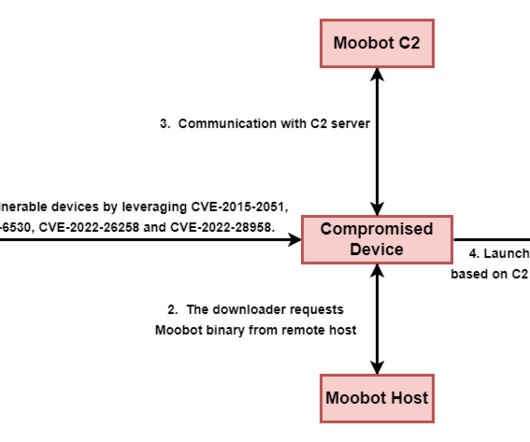
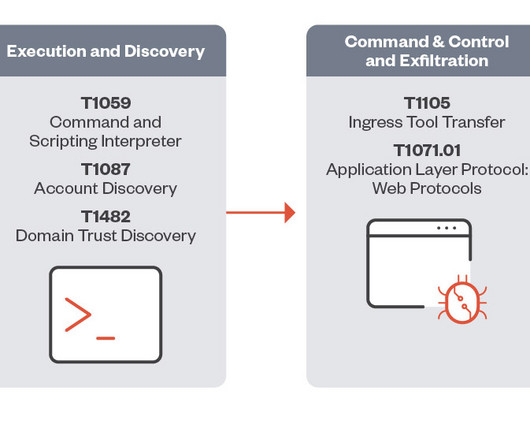
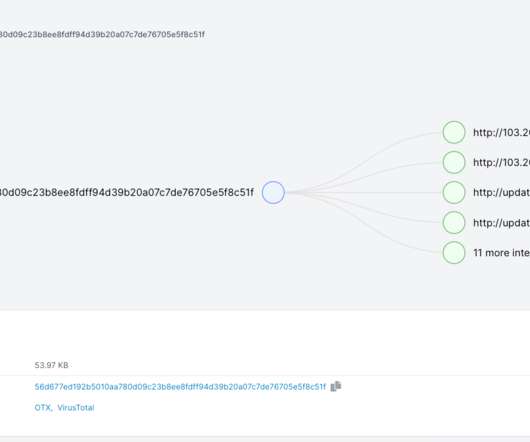
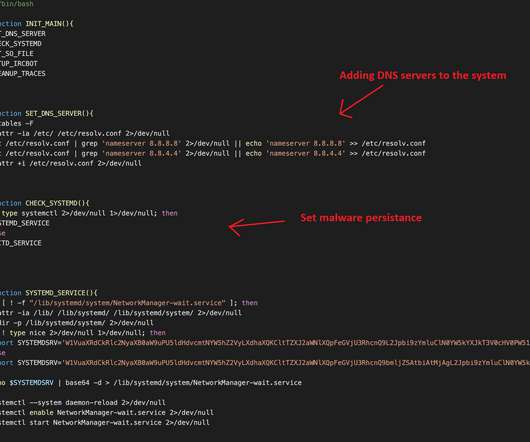
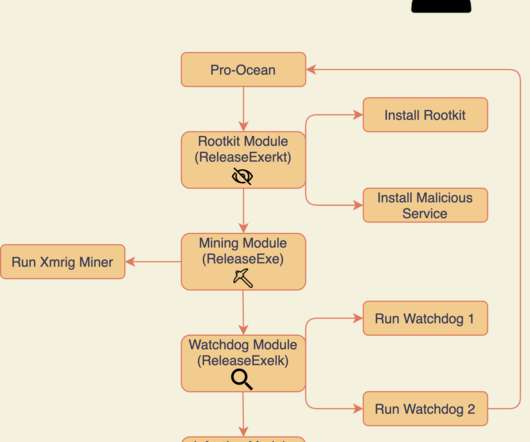
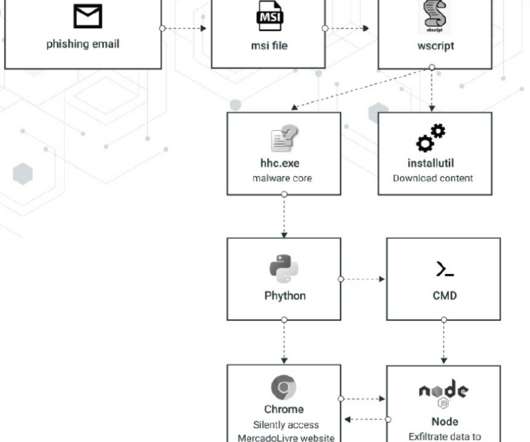
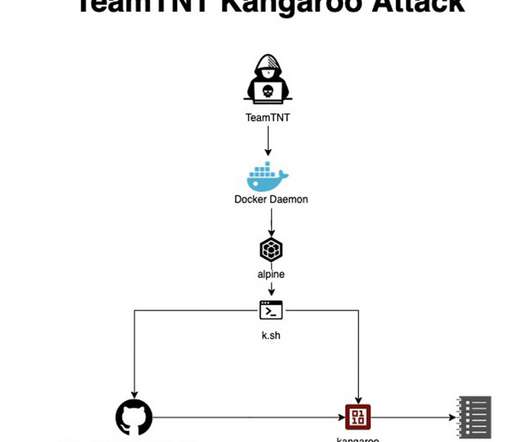
Trend Micro researchers reported that the EdgeRouter botnet , called Moobot , used by the APT28 group is still active and is also used by cyber criminal organizations. Trend Micro also discovered that at least two prominent cybercriminal groups and the Russia-linked APT group Pawn Storm used the botnet. ” reported Trend Micro.






































Let's personalize your content