Data Security Trends: 2024 Report Analysis
Thales Cloud Protection & Licensing
MARCH 24, 2024
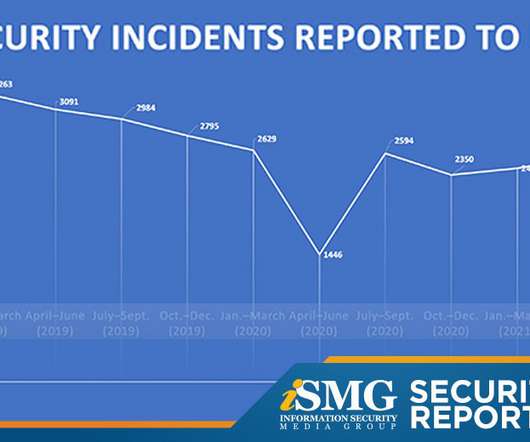
Data Security Trends: 2024 Report Analysis madhav Mon, 03/25/2024 - 05:08 Amid ongoing economic uncertainty and a progressively complex threat landscape, businesses are trying to navigate increasingly stringent regulatory requirements while bolstering their security posture. Next came Post Quantum Cryptography with 45%.









































Let's personalize your content