Use of Crypto Mining Pools to Launder Ransom Funds Grows 100,000% Over 5 Years
KnowBe4
JUNE 29, 2023
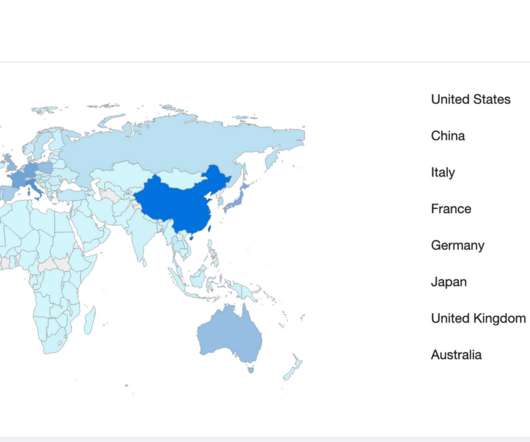
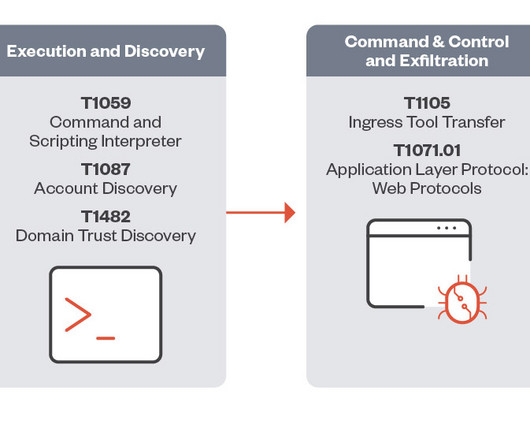
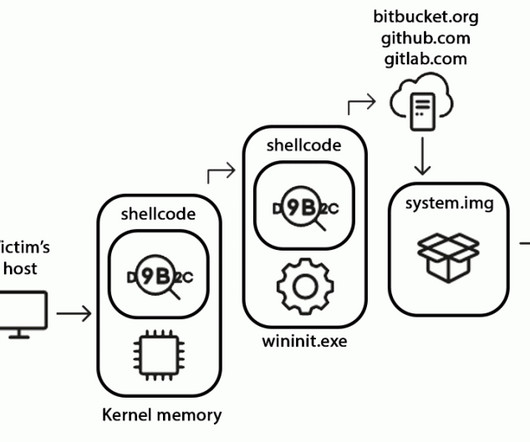
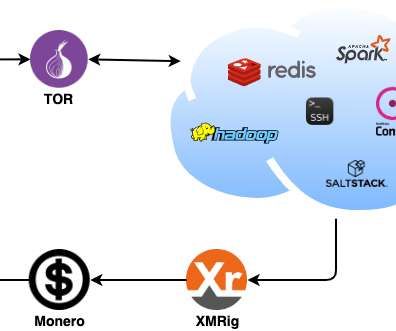
New analysis shows sources of cryptocurrency being placed into mining pools with huge deposits that make it easier for cybercriminals to make their ransom funds untraceable.









































Let's personalize your content