Is Cryptocurrency-Mining Malware Due for a Comeback?
Data Breach Today
JULY 16, 2021
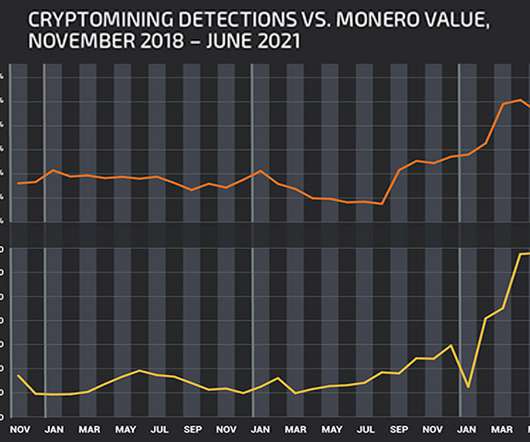
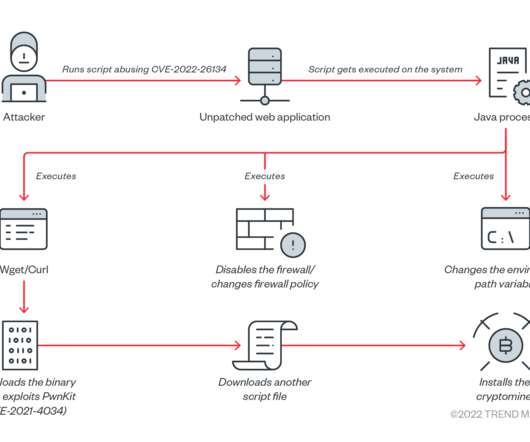
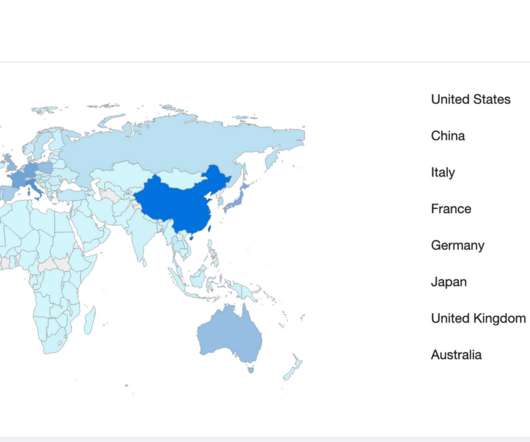
If Ransomware Should Decline as a Viable Criminal Business Model, What Comes Next? The world is now focused on ransomware, perhaps more so than any previous cybersecurity threat in history.







































Let's personalize your content