A phishing campaign targets Ukrainian military entities with drone manual lures
Security Affairs
SEPTEMBER 25, 2023
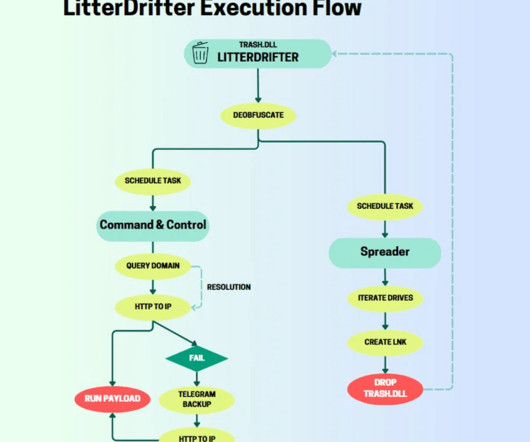
A phishing campaign targets Ukrainian military entities using drone manuals as lures to deliver the post-exploitation toolkit Merlin. The campaign, codenamed STARK#VORTEX by Securonix, targets Ukrainian military entities and CERT-UA attributed it to a threat actor tracked as UAC-0154. ” reads the analysis published by Securonix.

































Let's personalize your content