How to secure QNAP NAS devices? The vendor’s instructions
Security Affairs
JANUARY 7, 2022
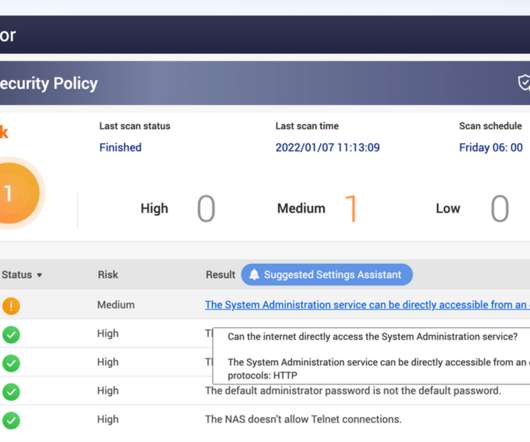
Taiwanese vendor QNAP has warned customers to secure network-attached storage (NAS) exposed online from ransomware and brute-force attacks. QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP networking devices.” The post How to secure QNAP NAS devices?









































Let's personalize your content