North Korea-linked Kimsuky APT attack targets victims via Messenger
Security Affairs
MAY 17, 2024
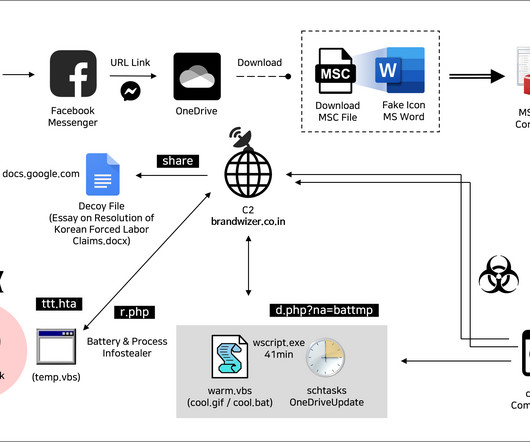
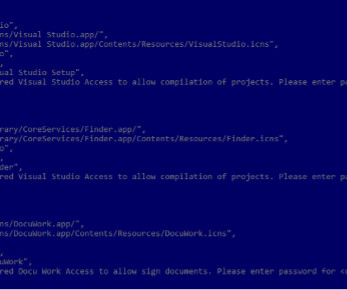
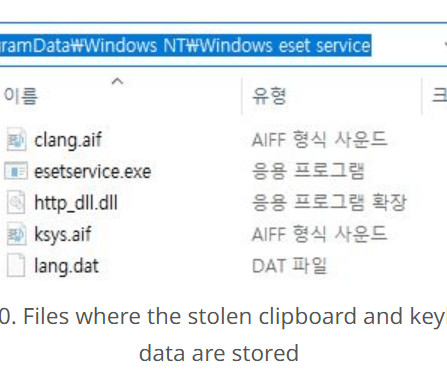
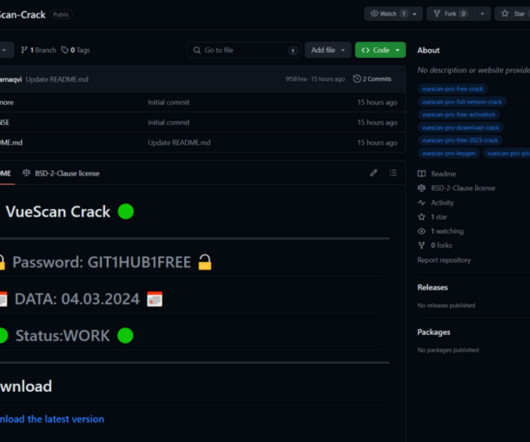
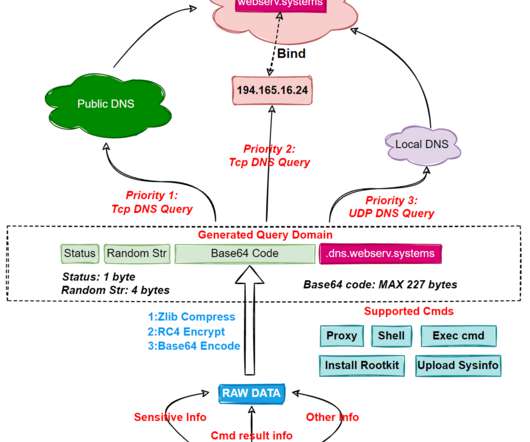
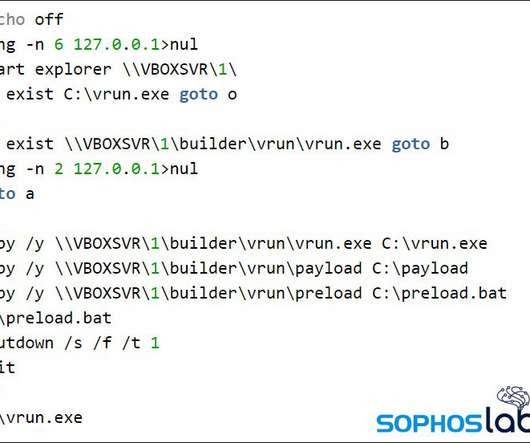
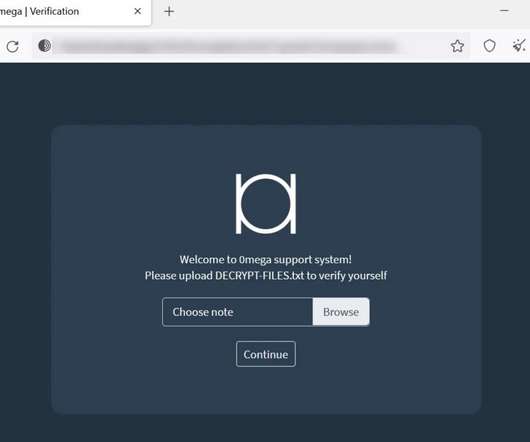
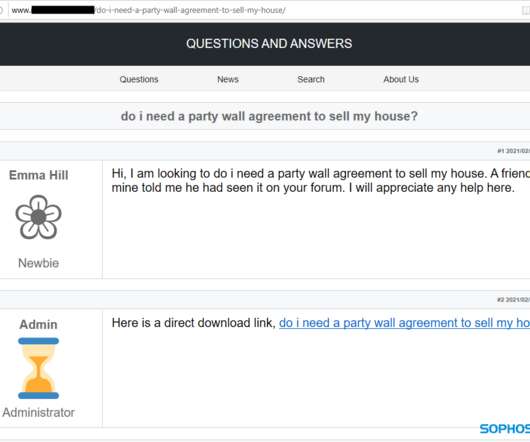
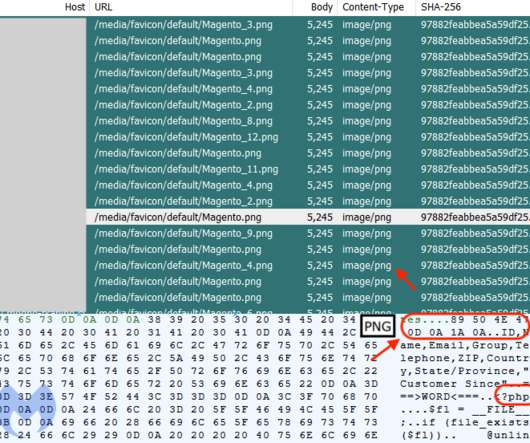
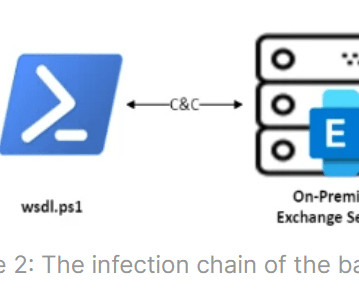
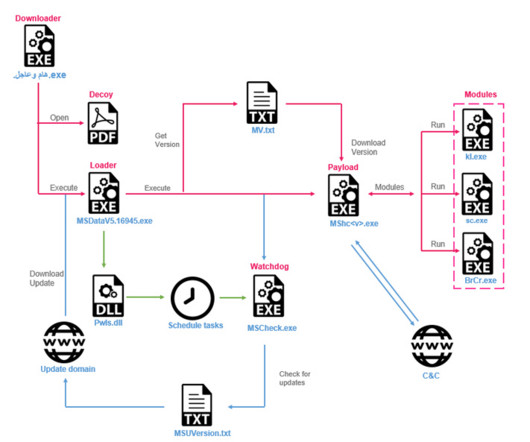
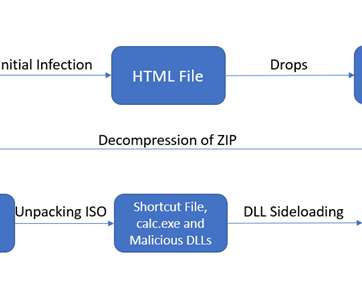
Researchers at Genius Security Center (GSC) identified a new attack strategy by the North Korea-linked Kimsuky APT group and collaborated with the Korea Internet & Security Agency (KISA) for analysis and response. ” reads the analysis. If the victims launch it the multi-stage attack chain starts.



















Let's personalize your content