Microsoft details techniques of Mac ransomware
Security Affairs
JANUARY 6, 2023
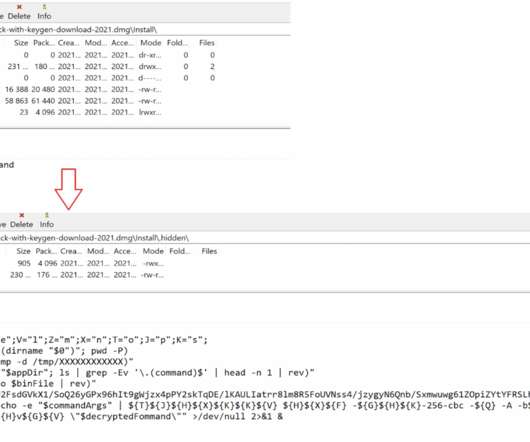
One of the most important capabilities of ransomware is the capability of targeting specific files to encrypt. FileCoder and MacRansom use the Linux find utility to search for selected files to encrypt. . “The ransomware families we analyzed often share similar anti-analysis and persistence techniques. _README_”. .










































Let's personalize your content