ViperSoftX uses more sophisticated encryption and anti-analysis techniques
Security Affairs
APRIL 29, 2023
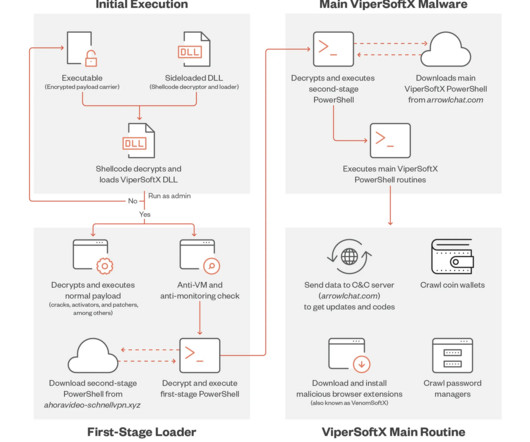
. “Without the correct byte map, the encrypted shellcode, including all components and relevant data, cannot be correctly decrypted, making decryption and analysis of the shellcode more time-consuming for analysts.” ” reads the analysis published by Trend Micro. ” concludes the report.




































Let's personalize your content