Cyber attacks hit the Assembly of the Republic of Albania and telecom company One Albania
Security Affairs
DECEMBER 29, 2023
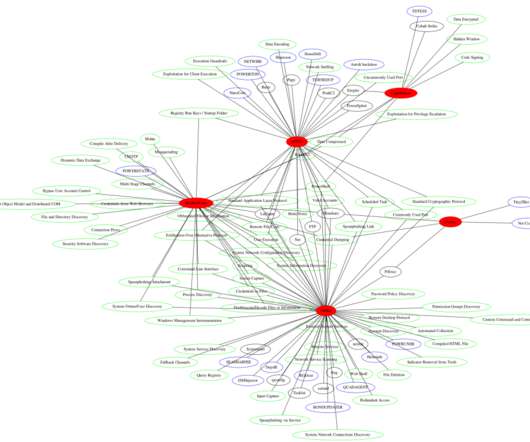
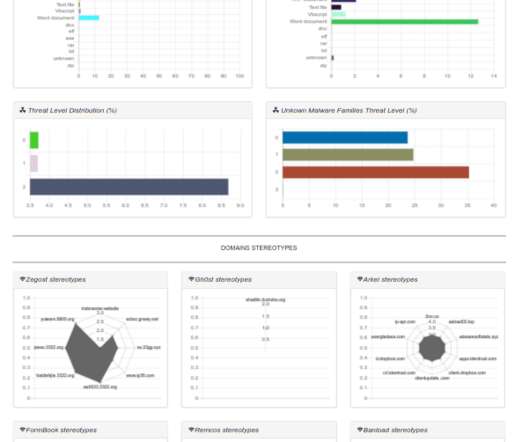
Cyber attacks hit the Assembly of the Republic of Albania and telecom company One Albania, a government agency reported. Albania’s National Authority for Electronic Certification and Cyber Security (AKCESK) revealed that cyber attacks hit the Assembly of the Republic of Albania and telecom company One Albania.









































Let's personalize your content