New US Electronic Warfare Platform
Schneier on Security
MAY 13, 2020
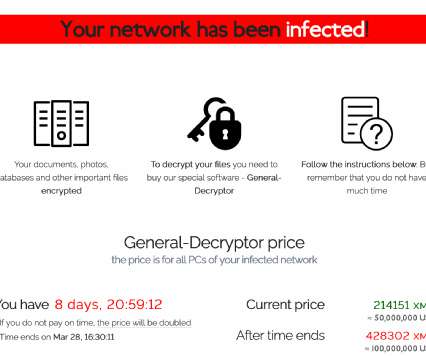
The Army is developing a new electronic warfare pod capable of being put on drones and on trucks.the Silent Crow pod is now the leading contender for the flying flagship of the Army's rebuilt electronic warfare force. Insiders call this cognitive electronic warfare ). The rise of wireless networks has caused the two to blur.











































Let's personalize your content