Facebook announces WhatsApp end-to-end encrypted (E2EE) backups
Security Affairs
SEPTEMBER 13, 2021
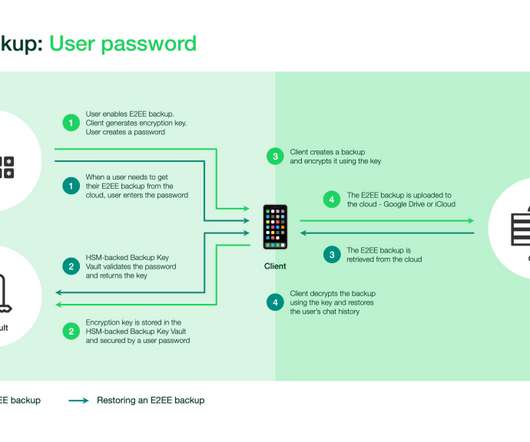
Facebook announced it will allow WhatsApp users to encrypt their message history backups in the cloud. Facebook will continue to work to protect the privacy of WhatsApp users and announced that it will allow users to encrypt their message history backups in the cloud. ” reads the announcement published by WhatsApp. .”










































Let's personalize your content