UK FCA Fines Equifax 11 Million Pounds for 2017 Data Breach
Data Breach Today
OCTOBER 13, 2023
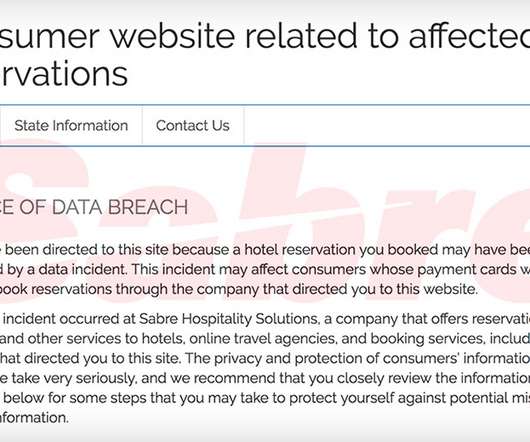
Chinese military hackers in 2017 exploited a well-known vulnerability in the company's online dispute portal. Fine Imposed for Failing to Protect UK Customer Data and Misleading Britons A British financial regulator fined American credit reporting agency Equifax 11 billion pounds for its role in one of the world's largest data breaches.










































Let's personalize your content