A PowerShell Script to Mitigate Active Directory Security Risks
eSecurity Planet
OCTOBER 12, 2023
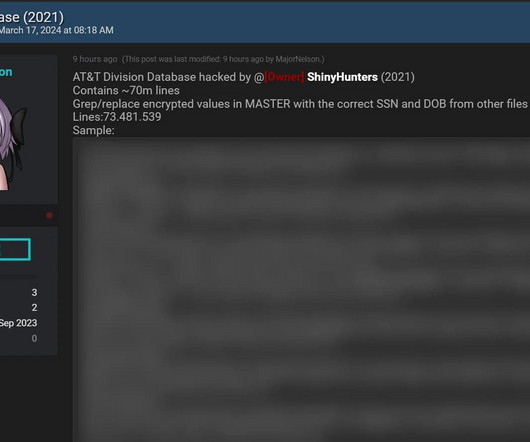
supports weak cryptography, which is a security risk as there are tools available to decrypt packets with weak cryptography. The client uses password hash to encrypt the challenge and sends it back to the domain controller as a “response.” which supports encryption and signing using weak hashing methods.













































Let's personalize your content