Horde Webmail Software is affected by a dangerous bug since 2012
Security Affairs
FEBRUARY 23, 2022
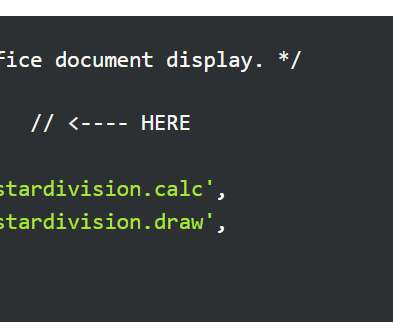
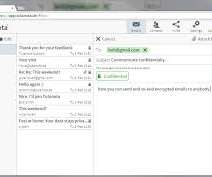
A feature in the Horde Webmail is affected by a nine-year-old unpatched security vulnerability that could be abused to gain complete access to email accounts simply by previewing an attachment. Horde Webmail is a free, enterprise-ready, and browser-based communication suite developed by the Horde project. ” continues the report.


































Let's personalize your content