Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
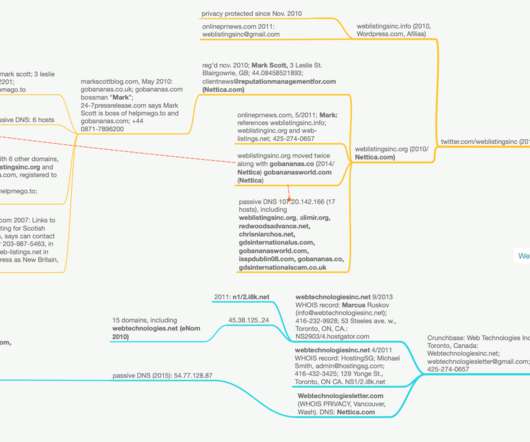
One from May 2011 at onlineprnews.com sings the praises of Weblistingsinc.info , weblistingsinc.org and web-listings.net in the same release, and lists the point of contact simply as “Mark.” Cached versions of this site from 2011 show it naming Web Listings Inc. as a business partner. That same management@helpmego.to





















Let's personalize your content