Administrator of RSOCKS Proxy Botnet Pleads Guilty
Krebs on Security
JANUARY 24, 2023
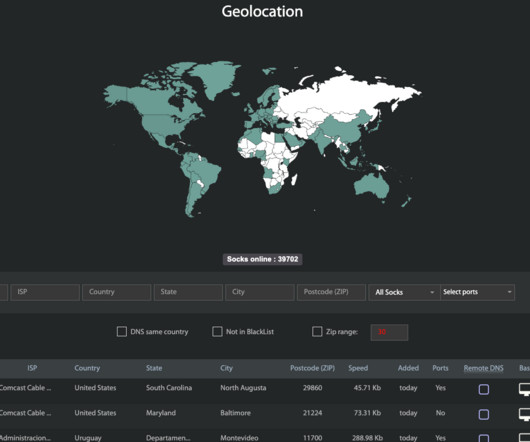
Many of the infected systems were Internet of Things (IoT) devices , including industrial control systems, time clocks, routers, audio/video streaming devices, and smart garage door openers. “Thanks to you, we are now developing in the field of information security and anonymity!,” Kloster’s blog enthused. “We


































Let's personalize your content