The Burden of Privacy In Discovery
Data Matters
SEPTEMBER 29, 2021
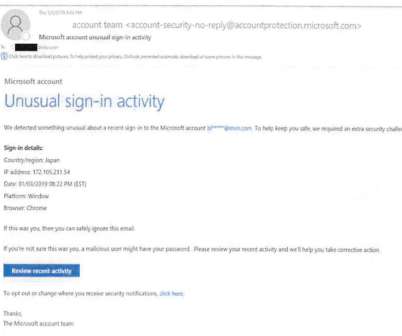
With the proliferation of social media platforms and other new technologies has come a renewed legal focus on privacy. Could a party, for instance, decline to produce, review, or even collect certain types of data due to privacy concerns? But what about other contexts? In this essay, Robert D.





























Let's personalize your content