Orchard botnet uses Bitcoin Transaction info to generate DGA domains
Security Affairs
AUGUST 8, 2022
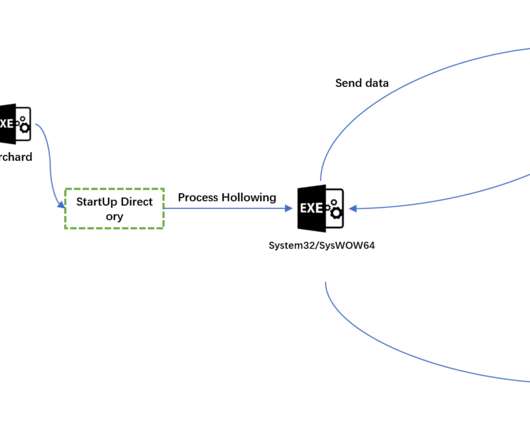
“It’s worth pointing out that the wallet address is the miner reward receiving address of the Bitcoin Genesis Block , which occurred on January 3, 2009, and is believed to be held by Nakamoto.” Version 3 supports features to launch an XMRig Monero mining software. Pierluigi Paganini.























Let's personalize your content