North Korean Hackers Look to Internet Explorer Zero Days
Data Breach Today
DECEMBER 7, 2022
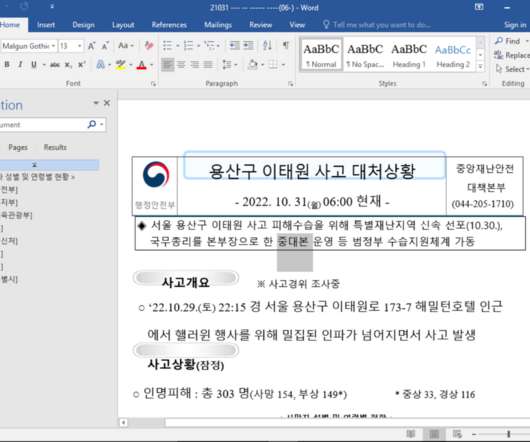
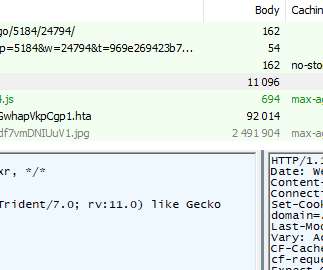
Google TAG Attributes Expoloits to State-Sponsored APT37, aka Reaper Microsoft Office's use of Internet Explorer to render HTML is the gift that keeps giving for North Korean hackers.









































Let's personalize your content