The iPhone 11 Pro’s Location Data Puzzler
Krebs on Security
DECEMBER 4, 2019
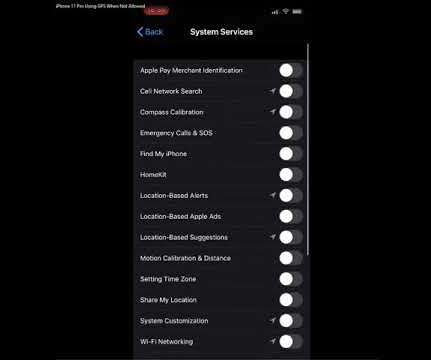
When one does this, the location services indicator — a small diagonal upward arrow to the left of the battery icon — no longer appears unless Location Services is re-enabled. “It is expected behavior that the Location Services icon appears in the status bar when Location Services is enabled.























Let's personalize your content