Russian Infostealer Gangs Steal 50 Million Passwords
eSecurity Planet
NOVEMBER 29, 2022
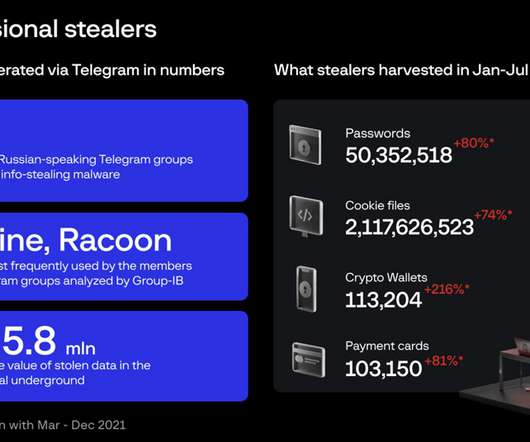
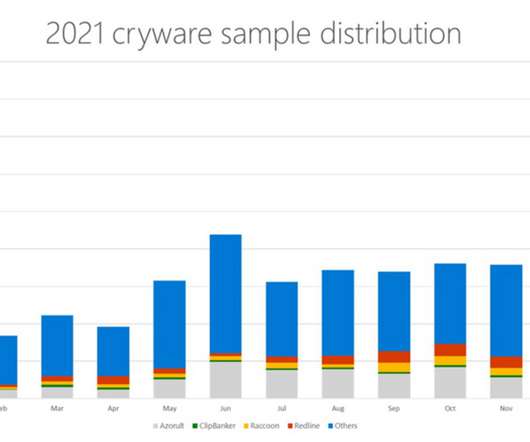
Group-IB cybersecurity researchers recently identified several Russian-speaking cybercrime groups offering infostealing malware-as-a-service (MaaS), resulting in the theft of more than 50 million passwords thus far. ” Also read: Complete Guide to Phishing Attacks: What Are the Different Types and Defenses? Last month, the U.S.













































Let's personalize your content