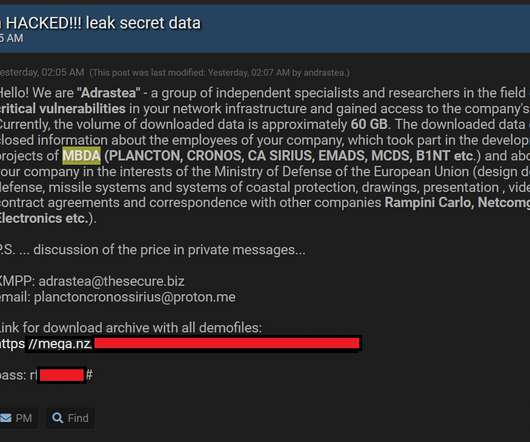
Threat actor claims to have hacked European manufacturer of missiles MBDA
Security Affairs
JULY 31, 2022
The attackers said that the stolen data includes information about the employees of the company involved in military projects, commercial activities, contract agreements and correspondence with other companies. Adrastea said that they have found critical vulnerabilities in the company infrastructure and have stolen 60 GB of confidential data.







































Let's personalize your content