Ukraine Fingers Russian Military Hackers for Kyivstar Outage
Data Breach Today
DECEMBER 13, 2023
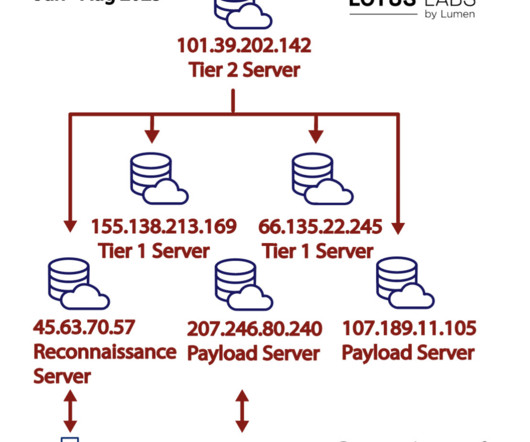
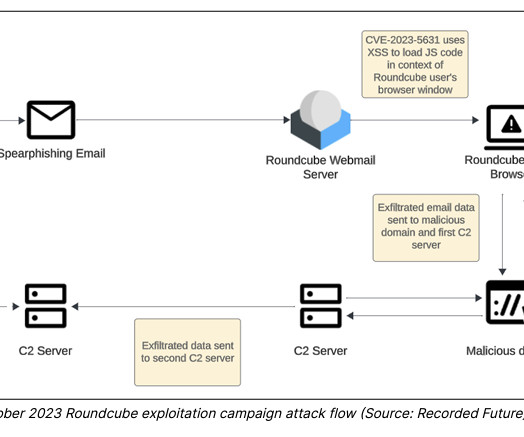
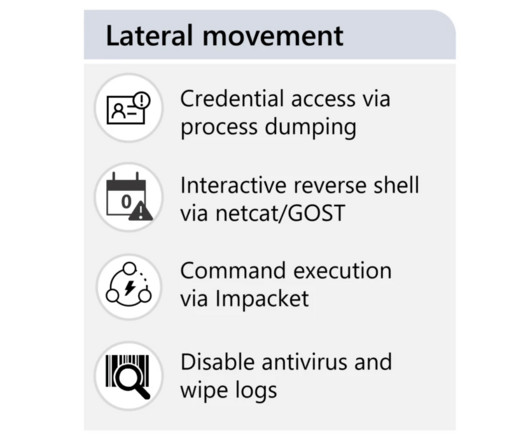
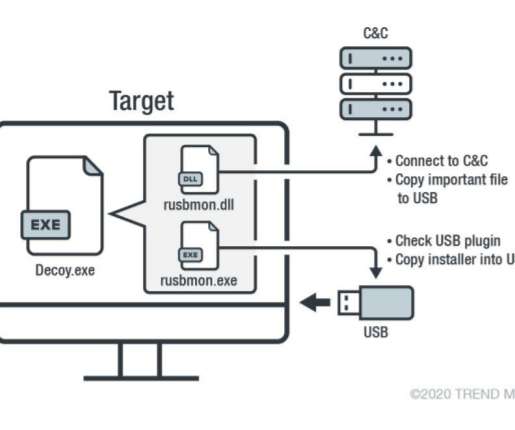
Telecom Operator Slowly Restores Voice Service Ukraine's domestic security agency on Wednesday fingered Russian military hackers as being responsible for hacking Kyivstar, in a statement acknowledging damage to the telecom operator's digital infrastructure. Ukraine's top telecom operator was the target of a Tuesday cyberattack.










































Let's personalize your content