Episode 245: How AI is remaking knowledge-based authentication
The Security Ledger
NOVEMBER 1, 2022
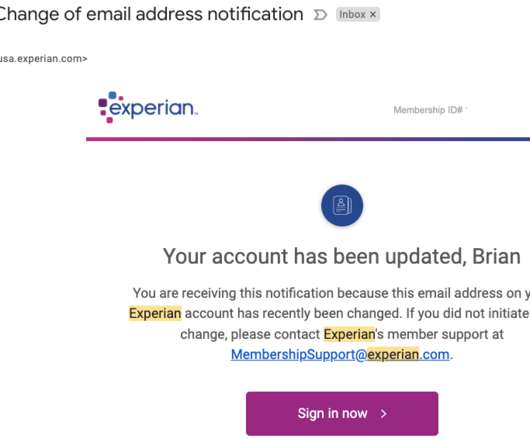
Six decades in, password use has tipped into the absurd, while two-factor authentication is showing its limits. We talk with Matt Salisbury of Honeybadger HQ, which is using AI and machine learning to re-imagine knowledge-based authentication. 60 years in, passwords at a breaking point. Read the whole entry. »


























Let's personalize your content