5 key areas for governments to responsibly deploy generative AI
IBM Big Data Hub
JANUARY 15, 2024
In 2024, the ongoing process of digitalization further enhances the efficiency of government programs and the effectiveness of policies, as detailed in a previous white paper. Only by doing so can governments establish themselves as trustworthy stewards.






























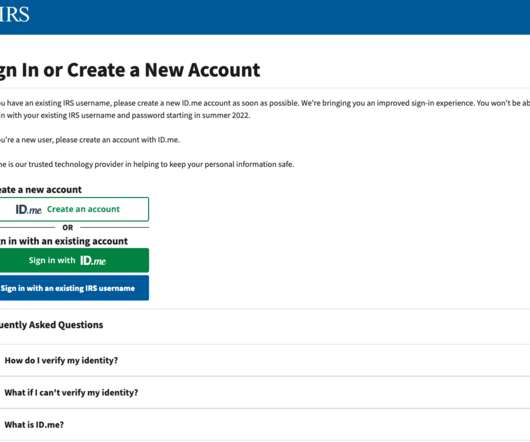







Let's personalize your content