FBI and CISA published a new advisory on AvosLocker ransomware
Security Affairs
OCTOBER 13, 2023
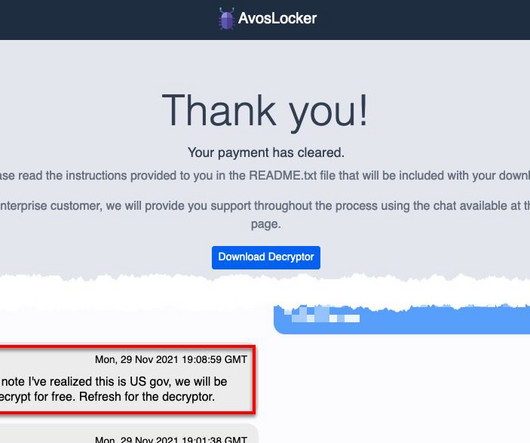
The AvosLocker ransomware-as-a-service emerged in the threat landscape in September 2021, since January the group expanded its targets by implementing support for encrypting Linux systems, specifically VMware ESXi servers. This joint CSA updates the advisory published by the US Government on March 17, 2022.












































Let's personalize your content