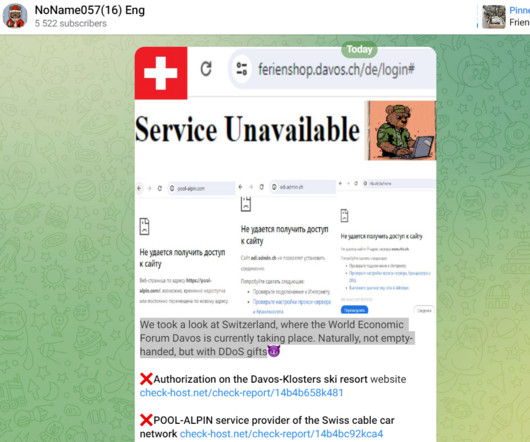
Meet the shady companies helping governments hack citizens’ phones via Fast Company
IG Guru
MARCH 1, 2024
The post Meet the shady companies helping governments hack citizens’ phones via Fast Company first appeared on IG GURU. Check out the article here.










































Let's personalize your content