Proactively Protecting Your Sensitive Information for Remote Workers
AIIM
JULY 8, 2021
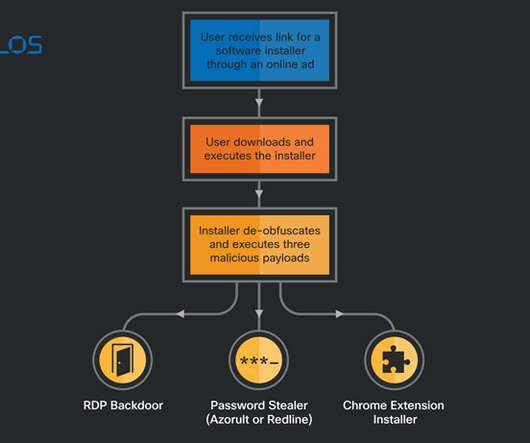
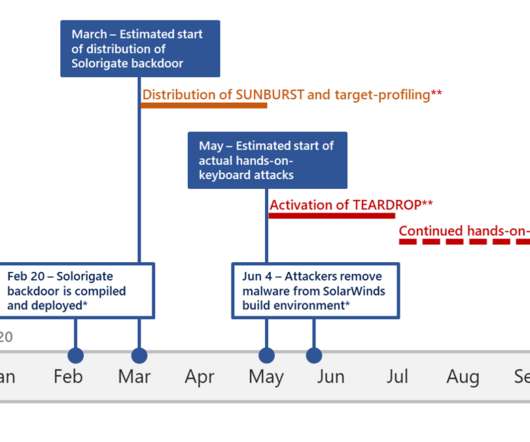
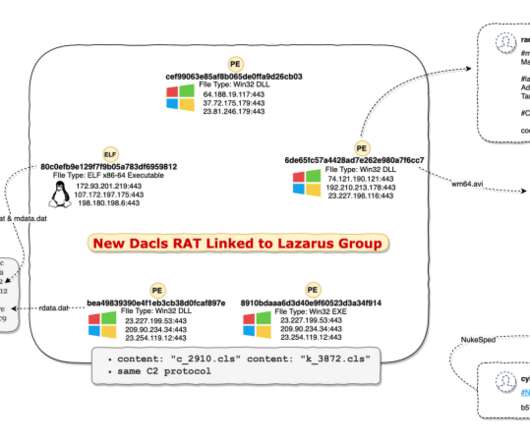
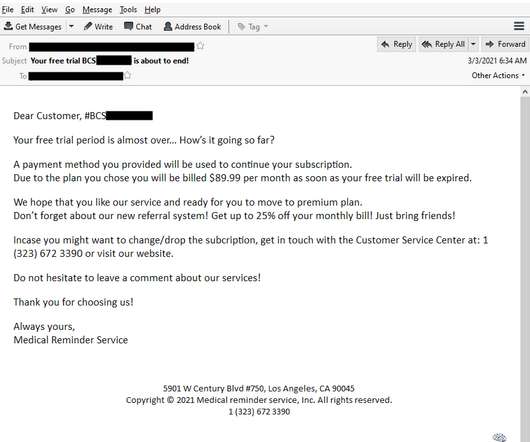
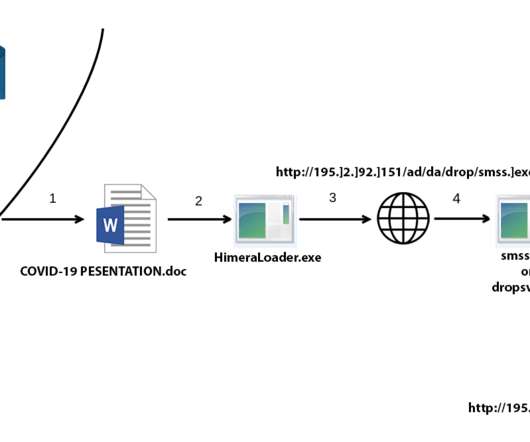
Don’t, however, lose sight of the fact that information scattered across a dispersed workforce can significantly raise the risk of a data breach or other security concerns. At Gimmal, we regularly talk to IT, security, and privacy professionals across a broad portfolio of industries. Applying retention rules (i.e.,


































Let's personalize your content