The risk of pasting confidential company data into ChatGPT
Security Affairs
MARCH 12, 2023
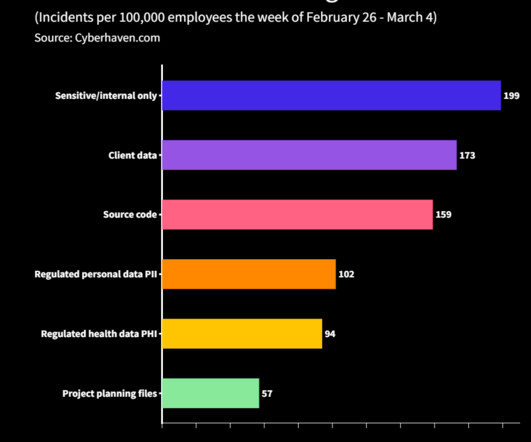
ChatGPT uses this data to build its knowledge base, but it publicly shares information built on it. This means that there is no inherent risk in using ChatGPT to discuss general issues or ask knowledge-related questions. They reported that 5.6% of them have used it in the workplace and 4.9%
















Let's personalize your content