Catches of the Month: Phishing Scams for April 2023
IT Governance
APRIL 11, 2023
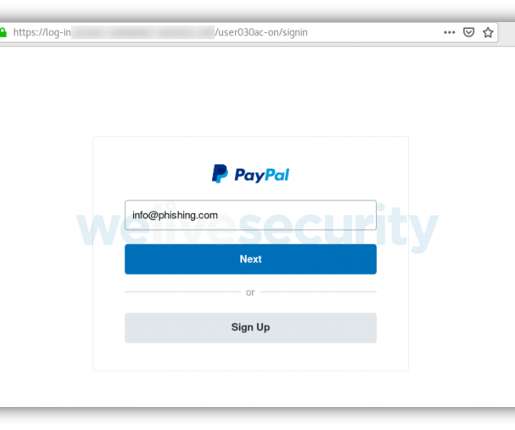
Welcome to our April 2023 review of phishing attacks, in which we explore the latest email scams and the tactics that cyber criminals use to trick people into handing over personal data. YouTube warns of monetisation scam Content creators on YouTube are being warned about a phishing campaign regarding an apparent “new monetisation policy”.


















































Let's personalize your content