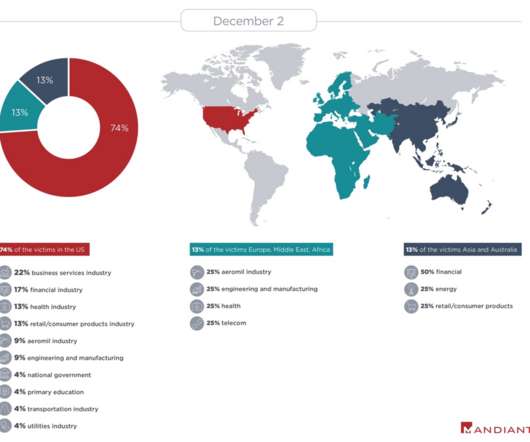
UNC2529, a new sophisticated cybercrime gang that targets U.S. orgs with 3 malware
Security Affairs
MAY 5, 2021
The attackers, who appear experienced and well resourced, employed custom lures and showed a professionally coding of their malware. The phishing messages include links to a malicious website that serves the malware, experts pointed out that the emails had subject lines that were customized for each targeted organization.


























Let's personalize your content